Side-Channel Attacks
May 23, 2016
I used a
cathode ray tube (CRT)
monitor on more than one
computer five years ago. The switch to
flat panel displays for my
desktop computing happened about a
decade ago; but, since many
laboratory instruments are seldom used, their change of monitors happened more slowly. My early computer readouts were from
octal LED displays and
Impact printers, but CRTs were a
de facto output device after the emergence of
personal computing in the late
1970s (
Apple II) and the early
1980s (
IBM Personal Computer). My first CRT was a small,
amber phosphor,
monochrome device attached to my
homebrew S-100-
CP/M system.
While nearly every CRT in existence has now been
recycled, everyone doing computer work had been using a CRT for several decades. All of these were based on the
raster scan principle used in
television receivers in which an
electron beam "paints" an image on a phosphor screen by scanning a line from left to right while moving slightly down, zipping back to the right, and repeating until the screen is filled. The
NTSC standard had 525 lines,
interlaced with odd and even lines sent on alternating frames at a 60
Hz refresh rate. The interlace was to prevent image flicker arising from the relatively slow refresh rate.
While special viewing screen attachments were available to prevent visual
eavesdropping on what you were doing (can't let the
manager see that you're playing
video games!), everyone was sure that their computing was
private in those days before
networks and the
Internet. As it turned out, the regularity of the raster signal and the way that it was implemented on CRTs allowed an easy means of electronically recreating the image on any screen at a distance through use of some inexpensive
circuitry.

A 14-inch cathode ray tube (CRT) with its deflection coils and electron gun highlighted
The electron beam has a power of about 1 watt, while the magnetic deflection coils consume tens of watts.
(Modified Wikimedia Commons image.)
Dutch computer scientist, Wim van Eck, whose original specialty was
bioengineering,
published a technique for doing what's now called
van Eck phreaking in 1985.[1] Such a vulnerability had been known to
governments since
World War II, when the target had been
teleprinters, not computers. In 1982, the US government had implemented a standard, called
Tempest, to make computer equipment immune to this technique. Van Eck had made the problem public to both
hackers and concerned users alike. Van Eck phreaking is a
plot element in my
novel,
Mother Wode.
Van Eck phreaking is an example of a
side-channel attack in which information about a computing device is inferred through measurement of some property. As a recent example, some
television and
movie plots have as a plot device
thermal imaging of
security keypads to determine which keys were recently pressed by warm fingers to thereby discover the
access code.
Van Eck phreaking wasn't the only side-channel vulnerability in early computer systems.
Light-emitting diodes designed to show
data activity on
modems were often wired directly to the data line. In such cases, the light was
modulated by the
data stream, and an
optical system would allow the data to be reconstructed. Early
wireless keyboards used a simple form of
encryption that was easily broken to reveal what you're typing through use of a
radio receiver.

An unlikely side-channel attack, as noted by science fiction author Neal Stephenson in his novel, Cryptonomicon, is looking at the wear pattern of keys on a keyboard. Unless the keyboard is used exclusively for typing of a password, this will likely just give the frequency of letter use of the language. In the portion of one of my keyboards shown above, you see that the key for the letter T is completely worn, and there's considerable wear on other letter keys. The letter T is the second most used letter (9.1%) in English. The first is the letter E (12.7%), which doesn't appear to be worn, somewhat invalidating this side-channel attack. (Photo by author.)
Your keyboard need not be wireless to leak information. Since different keys make slightly different
sounds when pressed, an
audio side-channel attack is possible. An easy method of defeating such an attack is to
mask the sounds with
white noise.
Audio susceptible to side-channel attack might come from unusual sources.
Multilayer ceramic capacitors typically use
barium titanate (BaTiO3) and other
ferroelectric materials as dielectrics because of their large
dielectric constant.
These ferroelectric materials are also
piezoelectric, which means that they will emit sound when the applied
voltage is changed. While the sound emitted by a capacitor is small, the
circuit board to which it's mounted will act as a
loudspeaker diaphragm to increase the sound
intensity. This "singing capacitor" effect has been addressed by at least one
manufacturer.[2]
Impact printers, in which
characters were stamped onto
paper much the way that
typewriters had always done, were prevalent in the early days of computing. One computer system with which I worked used a modified version of the popular
Selectric typewriter as a
printing terminal device, the
IBM 2741 printing computer terminal. It's easy to see how audio from such printers could be decoded in a side-channel attack. Modern
inkjet printers emit less audio, but a surreptitious
microphone, hidden in an
ink cartridge, could allow a side-channel attack.

A typeball from an IBM Selectric typewriter.
The IBM Selectric was an ingenious electromechanical typewriter that converted keypresses into pitch and rotation of a ball of type. These typeballs were interchangeable, which allowed a method to type mathematical symbols.
(Via Wikimedia Commons.)
Document printers aren't the only printers used in modern
development laboratories.
3-D printers are now used to make
product prototypes. Mara Hvistendahl reported on the
research of
Mohammad Abdullah Al Faruque, a
professor at the
University of California Irvine, and his
students on side-channel attacks on such printers.[3] The Irvine research team has presented its research at the
2016 Network and Distributed System Security Symposium (February, 2016),[4] and the
2016 ACM/IEEE International Conference on Cyber-Physical Systems (Vienna, Austria, April, 2016).[5-6]
Nearly every 3-D printer uses
stepper motors for positioning; and, as any user of stepper motors knows, these motors produce a lot of audio frequency sound. In fact, the stepper motors on various devices, including
computer disk drives, can play
music, as demonstrated on several
YouTube videos.[7-10] Says Al Faruque, "Industries spend millions of dollars to create IP (
intellectual property), and you can basically
steal it by listening to the machine."[3]
The research team printed
geometrical objects and a simplified
house key using a
Printrbot 3D printer.[5] By recording the machine sounds at a distance of 30 cm and using
audio analysis software, they were able to reproduce the
source code for the key to about 92%
accuracy.[3] While the
microphone placement for this exercise was near ideal, advanced techniques might make such a side-channel attack possible using a
smartphone for audio detection.[3]
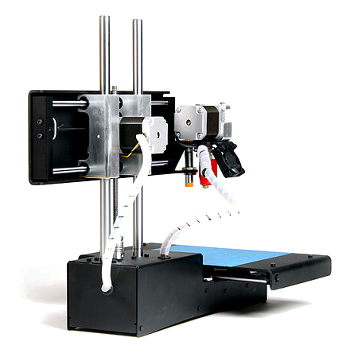
The Printrbot 3D printer.
The stepper motors for print head movement in the X and Z axes can be seen. Another motor drives the platen in the Y direction.
(Photograph by Creative Tools, Halmdstad, Sweden, via Wikimedia Commons.)
While this side-channel attack reveals geometrical information, it doesn't access the printer's other
parameters, such as
temperature and the
materials used. Just as for other audio side-channel attacks, interjection of white noise or
random stepper motor noise is a good
countermeasure.
References:
- Wim van Eck, "Electromagnetic radiation from video display units: An eavesdropping risk?" Computers & Security, vol. 4, no. 4 (December, 1985), pp. 269-286. A PDF file of this paper appears here.
- Mark Laps, Roy Grace, Bill Sloka, John Prymak, Xilin Xu, Pascal Pinceloup, Abhijit Gurav, Michael Randall, Philip Lessner, and Aziz Tajuddin, "Capacitors for Reduced Microphonics and Sound Emission," Electronic Components, Assemblies & Materials Association, CARTS 2007 Symposium Proceedings (Albuquerque, New Mexico, March, 2007).
- Mara Hvistendahl, "3D printers vulnerable to spying," Science, vol. 352, no. 6282 (April 8, 2016), pp. 132-133, DOI: 10.1126/science.352.6282.132.
- S. R. Chhetri, A. Canedo, and M. A. Al Faruque, "Poster: Exploiting Acoustic Side-Channel for Attack on Additive Manufacturing Systems", 2016 Network and Distributed System Security Symposium (February, 2016).
- M. A. Al Faruque, S. Chhetri, A. Canedo, J. Wan, "Acoustic Side-Channel Attacks on Additive Manufacturing Systems", 2016 ACM/IEEE International Conference on Cyber-Physical Systems (Vienna, Austria, April, 2016).
- Acoustic Side Channel Attack - Additive Manufacturing (3D-Printer), YouTube Video, January 5, 2016.
- Star Wars - Imperial March on Eight Floppy Drives, YouTube Video by MrSolidSnake, October 16, 2014.
- Stepmotor Super Mario Brothers, YouTube Video by Sam Buls, August 31, 2010.
- Toccata and Fugue in D Minor (On Floppy Drive Organ), YouTube Video by Sammy1Am, August 4, 2013.
- Imperial March on a CNC-Machine - Imperial March played on a Synchronous motor, YouTube Video by Dadido3, April 13, 2011.
Permanent Link to this article
Linked Keywords: Cathode ray tube; computer monitor; computer; flat panel display; desktop computer; desktop computing; decade; laboratory equipment; laboratory instrument; octal; light-emitting diode; LED; Impact printer; personal computer; personal computing; 1970s; Apple II; 1980s; IBM Personal Computer; amber color; phosphor; monochrome; homebrew; S-100 bus; CP/M; recycling; recycle; raster scan; television set; television receiver; cathode ray; electron beam; NTSC standard; interlaced video; hertz; Hz; eavesdropping; manager; video game; privacy; private; computer network; Internet; electronic circuit; circuitry; cathode ray tube; deflection; solenoid coil; electron gun; electric power; watt; magnetic field; Wikimedia Commons; Dutch; computer science; computer scientist; biological engineering; bioengineering; scientific literature; publish; van Eck phreaking; government; World War II; teleprinter; Tempest; hacker; plot narrative; plot element; novel; Mother Wode; side-channel attack; television program; film; movie; thermography; thermal imaging; electronic lock; security; keypad; access code; data; modem; modulation; modulate; data stream; optics; optical system; wireless keyboard; encryption; radio receiver; Neal Stephenson; Cryptonomicon; tribology; wear pattern; password; letter frequency; frequency of letter use; language; sound; acoustic cryptanalysis; audio side-channel attack; sound masking; white noise; audio signal; multilayer ceramic capacitor; barium titanate (BaTiO3); ferroelectricity; ferroelectric; relative permittivity; dielectric constant; piezoelectricity; piezoelectric; voltage; printed circuit board; loudspeaker; diaphragm; intensity; manufacturing; manufacturer; impact printer; ASCII; character; paper; typewriter; Selectric typewriter; computer terminal; printing terminal; IBM 2741 printing computer terminal; inkjet printer; microphone; ink cartridge; IBM; electromechanical typewriter; degrees of freedom; pitch and rotation; type; mathematical symbol; development; laboratory; 3-D printer; prototype; product; research; Mohammad Abdullah Al Faruque; professor; University of California, Irvine; postgraduate student; 2016 Network and Distributed System Security Symposium (February, 2016); 2016 ACM/IEEE International Conference on Cyber-Physical Systems (Vienna, Austria, April, 2016); stepper motor; disk storage; computer disk drive; music; YouTube; video clip; intellectual property; theft; geometry; geometrical; house key; Printrbot 3D printer; audio analysis; software; source code; accuracy; microphone; smartphone; print head; platen; Creative Tools; parameter; temperature; material; randomness; random; countermeasure.